Apple vs FBI should be the least of your concerns, because right now your emails, chats and files are not private, and they’re certainly not secure.
Not at home, and not at work.
If you’re like most internet-goers there’s a good chance you’re using some combination of Slack, Gmail, Dropbox or one of the many other popular message and file sharing apps on a daily basis; so why worry about Apple building backdoors into the iPhone if you’re perfectly content sharing your most sensitive messages and files through apps that already have the equivalent of built-in backdoors?
Value your privacy and security? If the answer’s yes, then you’re going to want to keep reading. And buckle up, because you’re in for a few surprises.
In this post we’re going to talk about how the communication, file sharing and file storage layers have become a huge security vulnerability for individuals and organizations of all sizes, why, and what you can do about it.
Your Privacy & Security at Work (is Lacking)
Still with us? Great, now let me ask you this:
What do the President of the United States, executives from Fortune 500 giant Sony, unicorn startup SnapChat, the Director of the CIA and officials from the Pentagon all have in common?
They’ve all had their emails, and consequently organizations, hacked within in the last year.
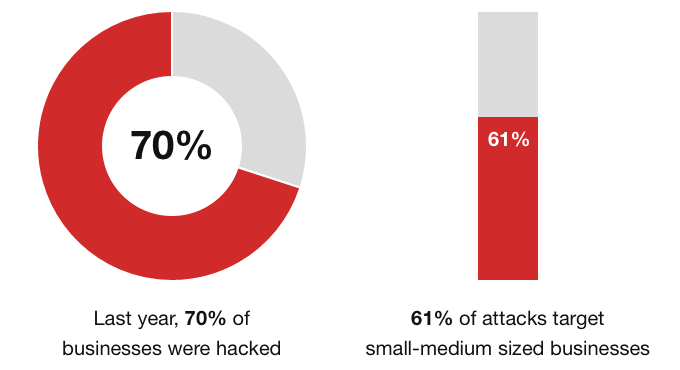
In fact, last year 70% of businesses were hacked [1].
Organizations of all types and sizes are targeted by hackers – not just the “big guys.” At 61%, the majority of attacks actually target companies classified as Startup through Medium sized business (a category your employer most likely falls into) [2].
Scariest part?
Most victims aren’t even aware that they’ve suffered a security breach.
That means there’s a good chance, a 70% chance, that your company was hacked last year without you knowing it. Yikes.
And it gets worse, because those hacks are costly.
By 2019 cyberattacks will cost businesses $2.1 trillion dollars in losses [3]. Yes, trillion.
And hackers aren’t just interested in stealing credit card numbers, identities and government secrets, no, theft of confidential business information is the third highest cost of these attacks [4].
Why should this concern you if you’re not a business owner and for some reason don’t care about your personal privacy?
Because when the company you work for gets hacked, your data is stolen as well.
Emails you’ve written, things you thought were shared in private, your social security number – all of it can end up in the wrong hands. The apps and services you use at work have a direct impact on you personally.
The reality is, hackers want what’s in your email. They want the files you share. They want everything, and right now, they’re getting it.
So who’s to blame for this mess?
Bottom line:
You, and your team at work, share a lot of sensitive information and files via email, Slack and dozens of other insecure apps everyday.
You are sharing and storing financials, proprietary info, passwords, even just ordinary conversations between co-workers or friends that – if they got out or were read out of context – could make you look really really bad (or even result in lawsuits).
These apps you’re relying on to protect your conversations and files are using insecure technology, often with purposely built-in backdoors (mostly used for literally spying on you and selling your information to marketers), and they’re leaving you exposed.
Most tech and app companies, even the ones touting buzzwords like “encryption,” are riddled with security vulnerabilities that hackers regularly take advantage of.
Clearly you’re in need of a better solution, and that’s exactly why we built ClearChat.
The Incumbents
Slack, HipChat, Dropbox, Gmail and others.
When it comes to protecting your data and your privacy, these companies are failing you miserably.
Bold statement? Yes.
But all of these companies have been hacked, some more than once, and they continue using insecure technologies to “protect” your data. And we’re not talking superficial hacks like websites or blogs being defaced, we’re talking about stolen customer passwords or data, and breeches of the applications themselves [5][6][7][8][9][10].

It’s time you knew.
Before diving in, let’s start by listing some common-sense items:
- If your email provider admits that they can and do read your emails, do you trust that they can keep your emails and files safe from hackers?
- If your provider is reading your emails – for marketing purposes or otherwise – that means there is a purposely built-in backdoor in their security setup so they themselves can spy on you.
- If that in and of itself doesn’t bother you enough, think about this: other people or nefarious organizations can figure out how to use that same security loophole to steal from you as well.
- If your provider openly sells your data to marketers, who else can get their hands on your information?
- If your “secure” messaging app has the following clause written in their own “security practices” policy, how can they can keep your data private or secure?
“The operation of the [Blank] services requires that some employees have access to the systems which store and process Customer Data… in order to diagnose a problem… we may need to access your Customer Data.” [11]
What??? Why even bother talking about “encryption” at this point if your provider blatantly admits they, from time to time, access your “private” conversations and files?
It’s not private if they are able to read it.
Libel? No. Unfortunate reality.
Look, I understand that this post is going to upset a lot of our very wealthy and powerful competitors (and yes, I am acknowledging that they are competitors), but 70% of businesses were hacked last year – our competitors just aren’t doing enough to protect your data, and your privacy.
We’re not here to make a blueprint on how to hack specific companies, but we are going to talk about some of the most glaring security flaws with almost all communication and file sharing applications on the market (for both consumers and businesses).
First, I’ll fill you in on some key information that, unless you’re a real cybersecurity enthusiast, you probably aren’t aware of:
- Not all “encryption” or encrypted apps are made equal.
- Hackers don’t break strong encryption itself, they “hack” companies/apps by finding “backdoors” (i.e. gaining access to usernames and passwords, encryption keys, etc.).
- As you’ll see below: encryption is easy; authentication is hard.
What does that mean?
It’s easy to “encrypt” data. With the keys, it’s also easy to decrypt data. It is not easy, however, to make sure that only the appropriate parties have the ability to decrypt the data. And as you’ll see below, in a world of spoofing, phishing and man-in-the-middle attacks, it’s also very difficult to “authenticate” that the person(s) you are speaking with, or sharing files with, is the person you think they are.
Okay, armed with this knowledge, let’s dive in:
TLS/SSL, “Encrypted in Transit”
TLS/SSL is the front-line of defense apps use to protect and encrypt your data.
“Despite TLS/SSL only originally being used for website logins and to protect financial information in-transit, it is now increasingly used for all TCP connections on the web with the goal of phasing out plain-HTTP completely. TLS seeks to encrypt data between a user and a server which has a domain name.” – Jonathan Warren, former CTO of ClearChat.com.
Sounds great right? In fact, many messaging apps solely rely on TLS/SSL for security.
We wont point any fingers.
The problem with this method?
“Because TLS encrypts communications between a user and a server, messages are necessarily decrypted at the server.”
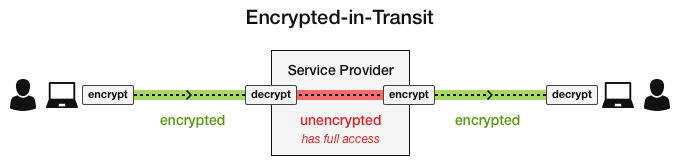
Ask yourself… if the competitor’s server can decrypt your messages/data… who else can?
“They may be re-encrypted and then stored on disk but this is almost useless; the server necessarily has the decryption key and must decrypt the data before sending it to the recipient.”
So if the server has the encryption keys, what happens when the server gets hacked?
The hacker gets the encryption keys, then decrypts and steals your data.
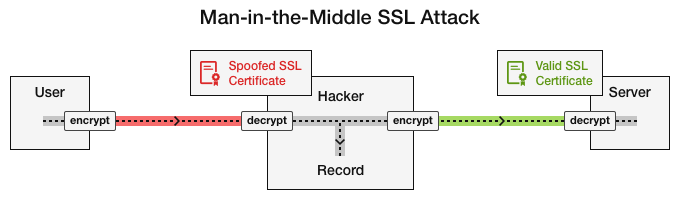
“TLS itself can be defeated either by an attacker with resources or by a rogue certificate authority. When connecting to a server over a TLS connection (like when using your browser to go to your bank’s website), your browser receives a public key from the server and must verify that it is the correct one. It does this by also receiving a certificate which is essentially a signed message from a certificate authority. The browser trusts the certificate authority either because that cert authority is trusted by a higher cert authority or because the cert authority is inherently trusted by the browser or underlying operating system (Mozilla, Microsoft, Google, ect.). Thus we have a giant hierarchy of trust.”
Okay great. Big hierarchy of trust from big name companies. You’re safe then, right?
No.
“Because so many (about a thousand) entities have the ability to sign certificates, that trust is frequently broken.”
I’m guessing you saw that one coming.
“In one incident, Iran used a fraudulent but mathematically valid certificate that was signed with the private key of a hacked certificate authority (DigiNotar) to conduct a man-in-the-middle attack against its citizens who were using Google services like Gmail [9][10].”
So, Iran “hacked” Gmail without hacking Google itself… instead they hacked a more vulnerable company and launched a man in the middle attack to intercept Gmail messages/data from unsuspecting users. Ouch.
“In another incident, an Egypt-based certificate authority ‘used the certificates in a man-in-the-middle proxy, a device that intercepts secure connections by masquerading as the intended destination.’ [12] One [unnamed] company even sells devices explicitly to break TLS and allows for the hand-off of SSL decrypted traffic to third-party monitoring and logging systems for analysis, archiving and network forensics.” [13]
In short:
If your app solely relies on TLS/SSL to protect your data, it’s just not enough.
And if your provider talks about re-encrypting data on their servers (at-rest encryption), but controls the keys (or their servers do), they’re in the same metaphorical boat. They control and have access to your “stuff,” not you.
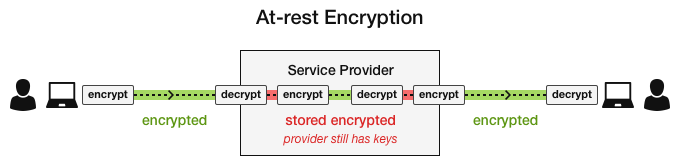
Relying on in-transit and/or at-rest encryption is not a solution to this problem.
What about PGP?
Ah, PGP. PGP is great, except for the fact that it has been in use for over 20 years and is nearly as difficult to use today as it was when it was first invented.
How many times have you ever used PGP – be honest with yourself? Once? Probably not even.
“Although PGP is considered perfectly secure when used correctly, using it correctly is uncommon. Users are supposed to check with one another to make sure that they are using the correct keys. They just usually don’t because they do not understand the need until it’s too late,” says Warren.
“Last year, one of Edward Snowden’s lawyers, Jesslyn Radack, sent an encrypted email to journalist Glenn Greenwald asking if Snowden was going to appear at the Polk Awards. By mistake, she sent the email to the public key of someone masquerading as Greenwald, who then decrypted the message and made it public.” [14]
Okay, so:
PGP is great, but…
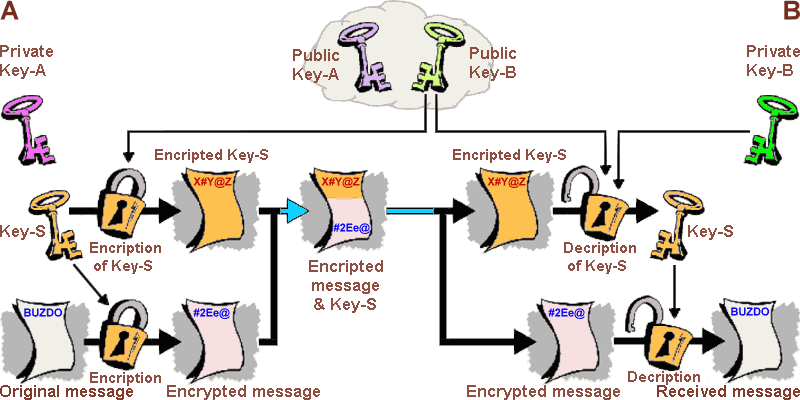
Whattt??? Img. credit: http://www.informatics.buzdo.com/extras/gpg-1.htm
Very few apps support PGP, and even fewer people understand how to use it. It’s just too complicated and too difficult for the average person to use.
If you are a business owner, good luck trying to get your employees to use PGP regularly – it won’t happen.
(Same goes for lawyers trying to use PGP with their clients, or a someone at work trying to share some sensitive files with you, etc. etc. It’s just too difficult.)
Phishing/Spoofing
Phishing, not the (boring, sorry) pastime, “fishing.”
A phishing “attack” is when hackers defraud people or companies online (often through email, or another communications channel) by posing as a legitimate company and confusing people to the point where they can’t tell the difference.
Phishing is often combined with spoofing, which is when the hackers imitate the company they are posing as by making their website, email address, or even caller ID appear to be coming from the legitimate company.
Many times, like in the case of the US Pentagon getting hacked [15], because it’s so hard to authenticate who the real sender of a message is through these apps, hackers can use unsophisticated attacks to dupe perfectly competent people into downloading malicious software or just plainly giving away sensitive information.
Did you know 97% of people can’t tell the difference between a real email and a phishing attack [16]?
It’s gotten so bad that even less technically savvy people have come to learn that you really can’t trust “who” an email is actually coming from.
What they don’t realize though, is that many of these “encrypted” apps, encrypted email providers, etc. can still be spoofed because they fail when it comes to authentication.
Even just think back to the PGP example with Snowden – a failure of authentication.
For those who haven’t learned this lesson yet, if you take nothing else away from this post, please heed this advice:
Do not give your password, or any other sensitive information about yourself or your business, to someone politely asking for it through email or on the phone.
(Even if you think it’s an email direct from Marc Zuckerberg, because “he needs to personally fix your Facebook account for you”… no. He’s not going to do that. No one from Facebook is going to do that. 600,000 Facebook accounts are hacked every single day [17].)
When you think an email is from “your boss” and she’s asking you to click a link or send him some files, you probably do it without hesitation. Hackers have picked up on that, which is why phishing and spoofing are so common.
The lesson here? You really shouldn’t be trusting the “from” fields in most email and messaging apps.
If Pentagon employees with top-secret clearance and cybersecurity training fall victim to phishing and spoofing attacks, I think it’s safe to assume that your team is just as vulnerable.
“Bank Level Security” and “Military Grade Security”
Companies love using buzzwords and terms that they think will comfort or pacify potential customers.
“You can trust us with your valuable data, because we use ‘bank level security.’”
In most cases, these really are just meaningless buzzwords and empty promises.
Banks use 256-bit AES and so do you? Great. That doesn’t mean your app is secure.
For the reasons pointed out in the sections above, time and again we see “bank level” and “military grade” “encryption” fall victim to hackers because of what amounts to built-in backdoors, and/or failures in authentication.
(Not to mention, banks and “the military” get hacked too.)
But what about X application I read about in the news that is so secure even the NSA/FBI want to ban it because they can’t break the encryption?
Which app? Hushmail [18]? iMessages [19]? ProtonMail [20]?
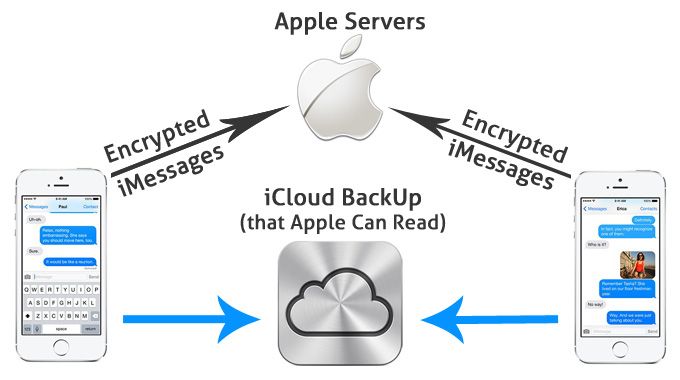
Img. credit: http://thehackernews.com/2016/01/apple-icloud-imessages.html
Unfortunately there really aren’t many easy to use end-to-end encrypted apps featuring real authentication and privacy – these encrypted apps are still vulnerable, and if the FBI needs help understanding that… well that’s actually rather disappointing.
Telegram? Unless you’re using the difficult to use “secrets” feature, unfortunately they’re just as vulnerable as the rest of them. And “secrets” is not ideal for use by teams or businesses – but I digress, this is a huge topic and discussion we’ll leave for another fiery blog post.
Bonus: Your Password Stinks (Probably)
Forgive my language, but applications that rely on password-based security are doing you a disservice.
In 2013 publisher, Ars Technica, hired a group of hackers to try and crack a list of 16,449 hashed passwords. End result? They did so at a 90% success rate in under an hour.
Even randomly generated 16 character passwords were cracked. That’s not good.
Are your passwords that strong? 16 randomly generated characters? Even if they are, which statistics suggest they’re probably not, they didn’t stand up too well to the real-world test.
Let’s be realistic, most people have short passwords that are easy to remember, and even easier for hackers to crack. Not only that, but despite knowing you should use unique passwords for every website/app you use, most people recycle the same handful of passwords all over the net, meaning when one site they frequent gets hacked they are exposed all over.
And as we discussed in the phishing section, 97% of people can’t tell the difference between a real email and a phishing scam, so people regularly just give their username and passwords away to hackers unintentionally.
It’s very easy for hackers to get their hands on, or crack your passwords, so if your app relies on password-based security you could be in for some trouble.
Bonus bonus: In an ideal world we’d all use apps that don’t rely on passwords for security, but that’s not possible in 2016. I don’t know about you, but my bank still requires me to have a password – so does Facebook, Twitter and most other apps. If you want some tips and information on keeping your accounts secure, go ahead and subscribe to our blog – we’re offering all subscribers a free guide on password security best practices.
Summary
While this is by no means a comprehensive dissertation on the security flaws in every messaging/file sharing app on the planet, it is a good primer.
For those interested in learning more, we’re happy to keep the conversation going.
As for our competitors who have fallen victim to the above mentioned security flaws, they are numerous and include some of the hottest names in the industry.
Some direct competitors such as Slack, Hipchat and Dropbox have already been hacked, often in just a few years of operations [5][6][7].
Others such as Gmail and Skype, in addition to suffering security breaches, flat out read all of your messages and offer you and your team little to no privacy [21][22].
I think you’re starting to understand that existing communication and file sharing/storage options for your team are flawed, and your data is currently in a very precarious position… so what do you do?
Good news, there really is a better way.
The Solution
Enter, ClearChat.
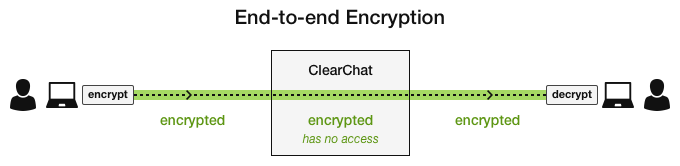
ClearChat is an application with patent-pending technology designed to be the first 100% end-to-end encrypted and authenticated message and file sharing app for teams.
Best part?
It’s designed to deliver this unprecedented level of security in an app easy enough for your least technical team member to use.
ClearChat looks and feels like the apps your team already loves using, but provides unrivaled privacy and security.
And here’s the kicker:
ClearChat is so private and secure, that we ourselves do not have the ability to decrypt messages or files sent by our own customers.
With ClearChat the only people who can see your data are the ones you explicitly intended to share it with.
Encryption is easy; authentication is hard?
Not anymore. Not with ClearChat.
Even if ClearChat’s own servers get hacked, the hackers will not be able to decrypt your data because our servers and our staff do not have your encryption keys.
How can we succeed where others have failed?
Because we’ve built an entirely new communications protocol based on complex cryptography – our security methodology has been beta tested through a prototype for the past 3 years by more than 15,000 users, securing over 130,000 messages per month.
Our prototype, with widely reviewed open source code, has been dubbed, more secure than gmail by CNET [paraphrased, 23], and even “NSA-proof” by Bloomberg news [24].
The prototype for ClearChat, called Bitmessage, was invented by our former CTO, Jonathan Warren.
Img. credit: http://www.bloomberg.com/bw/articles/2013-06-27/bitmessages-nsa-proof-e-mail
What’s the difference between Bitmessage and ClearChat?
Bitmessage is a tool designed to function similar to email, and is for use by more technically inclined individuals/consumers.
ClearChat is designed as a secure group/private chat + file sharing application for teams, businesses and governments.
(We will be doing a separate post on ClearChat’s technical relation to Bitmessage, and to Bitcoin, which heavily inspired Bitmessage’s technology. For now, you can read about how ClearChat works under the hood. We’ll even be open sourcing the most important parts of our code for anyone to review on their own.)
Why model ClearChat as a team chat and file sharing application instead of modeling it more closely after email, or its predecessor Bitmessage?
Well, answer this question:
What is the fastest growing business software company of all time?
Answer: Slack.
With a valuation of $2.8Billion+ in less than 3 years of operations (even though they’ve already been hacked), they hold the title [25][26].
Translation?
Teams around the world have “spoken;” by making Slack (and competitor Hipchat) grow like wildfire, it’s clear that people prefer chat apps for team communication and collaboration over email.
So we listened.
ClearChat looks/feels/functions similarly to the chat/messaging apps you already know and love, but unlike those apps, it’s secure and provides your team (and each individual on your team), privacy.
Store or share files end-to-end encrypted with ClearChat, have private conversations with friends, coworkers or suppliers that are actually private (and not being snooped on by a mass surveillance program or even your own service provider), and permanently delete any message or file you’ve ever sent with a click of a button.
ClearChat even supports private/secure communication and file sharing with people outside of your organization, through a feature called, “guest users.”
What about “Bad Actors?”
But wait – if ClearChat is so secure that even the company operators themselves can’t access the messages/files of clients, does that mean it can be used by bad people to do bad things?
We’ve thought about this extensively, and will be doing everything within our control to provide an encrypted, private and authenticated platform while still preventing nefarious activity.
For starters, while by design ClearChat simply cannot, in any way, provide law enforcement with “backdoors” to our clients’ data, we can and will comply with the United States legal system if/when subpoenaed for information.
Whoa whoa, what do I mean? Backdoor for the feds? What about privacy?
No, like I said, we can’t do that even if we wanted to (which we don’t).
What we can do, is if ClearChat receives a subpoena for information on a certain client, while we can’t provide the court with any actual data or files, we can point them in the right direction. We can tell them which door to knock on next (the client themself). It then becomes an issue between the government and the client.
ClearChat is not designed to be a platform for anonymous users and hacker groups – it’s a tool for legitimate teams, businesses and organizations.
By default, to accept payments in the United States, we have to “know our customer.”
With anti-fraud systems coupled with know your customer policies, and even blocking entire regions of the world from being able to use our application (unfortunately), we will do our part.
We understand what a powerful tool ClearChat is, and will do everything we can to be a good actor, an innovator who protects other good actors, and not a harbor for bad ones.
There’s no backdoor, but we are law abiding American citizens wishing to operate an innovative tech company in good faith here in the United States of America.
Conclusion
Existing email, chat and file sharing/storage apps are widely vulnerable to hackers.
With 70% of businesses hacked last year, and the cost of cybercrime reaching $2+ trillion in losses by 2019, this is a fire in desperate need of an extinguisher.
Today, your email, chats and files are not secure. Your company’s data is not secure. You have limited to no privacy with your current cloud storage and communications providers. If your company is not “on fire yet,” there’s approximately a 70% chance it will be by the end of the year.
ClearChat is the only end-to-end encrypted, private and authenticated app built for teams, businesses and organizations.
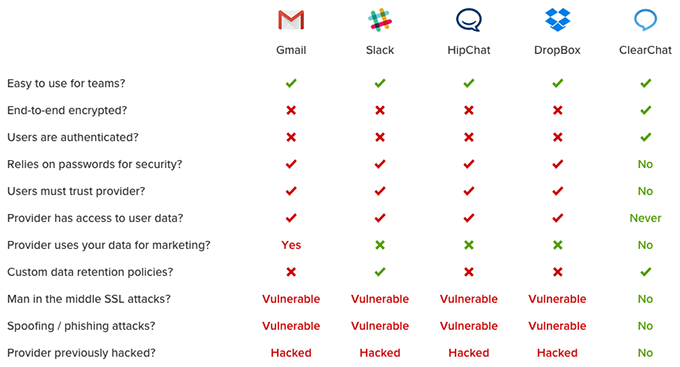
While ClearChat is not the end-all be-all cybersecurity solution, ClearChat can effectively limit your exposure to cybercrime and financial risk, and offer you an unprecedented level of privacy, by protecting your very vulnerable communication and file sharing/storage layers.
ClearChat cannot be spoofed (like email and websites), doesn’t rely on root certificate authorities or TLS/SSL (like our competitors), and customer messages/files cannot be decrypted even if our own servers become compromised by a hacker.
Do yourself, and your team, a favor – clear your inbox, improve your bottom line and protect your business, with ClearChat. Take back your privacy.
Questions? Concerns?
Want to learn more or fervently debate the nuances of cybersecurity?
Leave a comment below, reach out to us on social media, or signup to apply for our fully functional beta (limited availability, completely free to use while in beta).
In this war on cybersecurity and privacy, we’re all in this together – stay safe!
PS. Please note that we have tremendous admiration and respect for our innovative competitors who have paved the way for us to build an app like ClearChat.
We do not want to see them hacked, nor do we want to see them fail. We do want to see them do a better job at protecting their customers, and if they want or need our help, they can reach out.
PS. #2/Disclaimer: This post is a expression of our opinions. If you want to dispute any of the information or claims, please feel free to do so. Compile your own research, leave a comment, tell us what you think – we encourage it.
References
- Rosalie L. Donlon, Property Casualty 360, “Almost 70% of businesses have been hacked in the last year, and 36% have no cyber coverage,” 2015
- Symantec, “Internet Security Threat Report,” 2014.
- Juniper Research, “Cybercrime will cost businesses over $2 trillion by 2019,” 2015
- McAfee, “Net Losses: Estimating the Global Cost of Cybercrime Economic impact of cybercrime II,” 2014
- Greg Kumparak, TechCrunch, “Slack Got Hacked,” 2015
- Paul Ducklin, Naked Security by Sophos, “Hackers breach password database at Atlassian’s ‘HipChat’ collaboration service,” 2015
- Ed Bott, ZDNet, “Dropbox gets hacked… again,” 2012
- Zach Epstein, BGR, “How to find out if your Google login was compromised in the Gmail Hack,” 2014
- Elinor Mills, CNET, “Fraudulent Google certificate points to Internet attack,” 2011
- Heather Adkins, Google Online Security Blog, “An update on attempted man-in-the-middle attacks,” 2011
- Reference provided privately upon request
- Dan Goodin, Ars Technica, “Google Chrome will banish Chinese certificate authority for breach of trust,” 2015
- Reference provided privately upon request
- Cryptome, “Radack – Greenwald,” 2014
- Richard Lawler, Engadget, “Russia apparently gets the blame for hacking the Pentagon email,” 2015
- McAfee, “97% of People Globally Unable to Correctly Identify Phishing Emails,” 2015
- Sarah Perez, TechCrunch, “Facebook sees 600,000 Compromised Logins Per Day,” 2011
- Ryan Singel, Wired, “Encrypted E-mail Company Hushmail Spills to Feds,” 2007
- Swati Khandelwal, The Hacker News, “Apple Can Still Read Your End-to-End Encrypted iMessages,” 2016
- Yael Grauer, Wired, “Mr. Robo Uses Protonmail, but it Sill Isn’t Fully Secure,” 2015
- Eileen Brown, ZDNet, “So Facebook allegedly reads your private messages. But what about Google?,” 2014
- John Koetsier, Venture Beat, “Busted: Microsoft intercepts, decrypts, and reads your Skype messages,” 2013
- Molly Wood, CNET, “Gmail: You weren’t really expecting privacy, were you?” 2013
- Max Raskin, Bloomberg Business, “Bitmessage’s NSA-proof E-mail,” 2013
- Jillian, D’Onfro, Business Insider, “2.8 billion Slack has turned down 8 to 10 acquisition offers,” 2015
- Casey Newton, The Verge, “Slack is now the fastest growing workplace software ever,” 2014
 Brendan Diaz
Brendan Diaz