“Our money is safer under the mattress than it is in the community bank!”
We all sort of laughed at my neighbor’s conclusion to the philosophical discussion about current banking cyber crimes. About five of us were tossing around our perceptions of the cyber readiness of financial institutions when Chris decided we should just take all our money out. Of course, we were being a bit fantastical and just having fun with our dramatized cyber doomsday scenarios. And I don’t think Chris was serious about keeping his money under a mattress.
But the truth is, many banks are struggling to keep up with information security. And the terrifying truth is, a lot of their efforts are trailing behind hackers’ capabilities.
Consider this.
Community Bank
Jeremy has been working at a community bank for 12 years. He loves his job. He’s always been a process and detail oriented type person, so his work falls right in line with his personality. Moreover, he feels like a real part of his community. Working at a community bank means he gets to know his customers personally. He watches their children grow up and reaches out to them on important milestones.
Jeremy’s community bank prides itself on friendly and personalized services. They top that off by making all banking decisions in-house.
To them, customers are more than just a number. Jeremy is proud to be part of that culture and a true member of his community.
After a long holiday weekend, Jeremy settles into his desk and starts prepping for his day. But before he can look at his email, he notices his supervisor briskly walking up to him with a flushed face, wide eyes, and strange empty gaze.
Before Jeremy can tell his supervisor to go home and get some rest, his co-worker leans over and whispers, “There was a breach.”
A breach?
Over the weekend, someone gained access to several customer accounts and started withdrawing money. They counted over $500,000 lost already.
Everyone at the bank is reeling. Who would do this? What about the customers? When can we get their money back? How did this happen?
HOW DID THIS HAPPEN!?
It takes a couple of weeks before investigators are able to answer that question. As it turns out, hackers infiltrated a computer with management-level access to customer accounts and bank cards.
And how did hackers gain access to that computer?
Email.
These attackers sent a targeted phishing email to an employee with high-level access. After infecting that employee’s computer with malware, they were able to compromise a second computer within the bank. The second computer housed a trove a highly sensitive financial information and accesses, thus enabling the hackers to get away with hundreds of thousands of customer dollars.
Jeremy is always so diligent in his duties at the bank. He takes them very seriously and feels a real connection, responsibility, and obligation to his customers.
He couldn’t believe he fell victim to a spear phishing email. Nothing in his inbox seemed suspicious. Nothing stood out. Even thinking back on it, he isn’t sure he remembers the infected message at all.
Jeremy was devastated when the investigation revealed his email account facilitated the breach.
Community Bank Hacking
Think Jeremy’s story is far fetched? It happens far too often. It happened at a Blacksburg, VA bank twice within eight months just last year.
While hackers target all financiers, local and community banks are becoming more frequent marks…
and email attacks are a weapon of choice.
The truth is cyber bank theft is a daily occurrence, and the rate of breaches at financial services institutions (FSIs) has tripled in the past five years. According to a recent study by Accenture, a bank encounters about 85 cyber attacks each year.
At least 1/3 of them are successful.
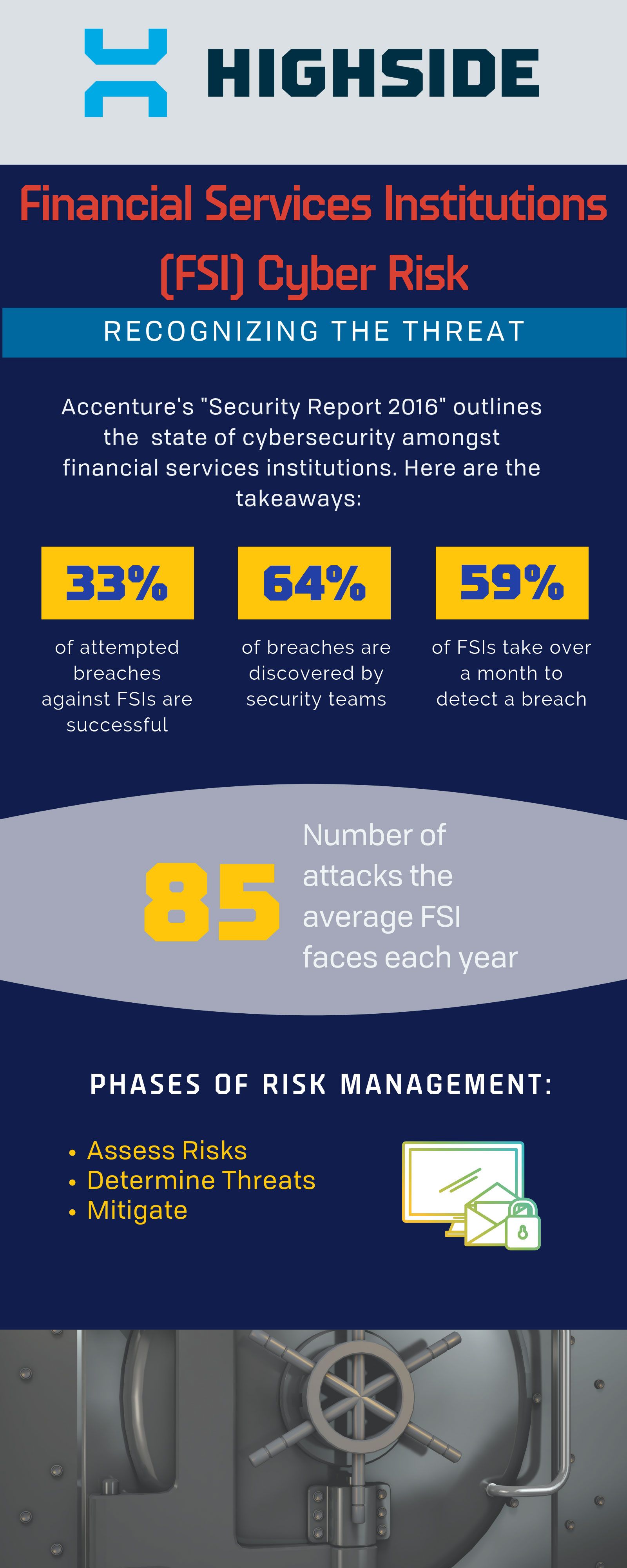
To make matters worse, the cost of those breaches has increased more than 40% over the past several years. Now, cyber incidents at FSIs are more expensive than in any other industry.
And when hundreds or hundreds of thousands of customers have money connected to the same system, an attack against one part of the system (or one person in the system) becomes an attack against the whole system, leaving everyone’s money and data at risk.
The recent JP Morgan hack is a key example. In 2014, JP Morgan suffered a breach that affected about 7 million small businesses and 76 million individuals. According to insiders, hackers stole an employee’s log-in credentials via malware installed from a phishing attack.
In that case, a single email led to the biggest bank breach in history.
Some look at the JP Morgan hack and conclude that cyber criminals only target big banks, and smaller community banks are immune. They think because community banks have fewer resources, they have fewer opportunities for cyber attacks and are more likely to successfully defend their assets. They argue that because smaller banks have fewer assets, they’re less attractive targets for hackers.
Unfortunately, those naysayers are wrong. Hackers are successfully attacking community banks more frequently. Sophisticated cyber thieves are moving away from bigger institutions and using their resources on “softer targets”.
Why?
After the JP Morgan breach, big banks were able to justify spending more money on cybersecurity. They invested in more research and greater protections, making them harder to penetrate. As a result, many hackers started looking at other targets as easier prey. And many smaller banks can’t invest in cybersecurity the way bigger institutions can. So instead of the JP Morgans, hackers are now looking at community banks, credit unions, real estate attorneys, and other mid-tier financiers.
When asked about cybersecurity and small banks, finance expert Sean Niquette says, “Small banks often have to balance between regulatory burdens on capital and investing in IT security infrastructure.” He explains that the balancing act has left many smaller banks lagging behind in security.
Regulators support his stance. The Federal Reserve of Boston and other regulatory bodies urge that smaller banks are at the greatest risk of cyber attacks.
Hacking Methods
Cyber criminals use many attack patterns to access banking institutions. Of them, the most popular (and most successful) are business email compromise (BEC) and man-in-the-middle attacks.
BEC Attacks
BEC attacks are targeted communications attacks that use a variety of methods, including phishing, spoofing, and social engineering. Specific examples include:
- Employee impersonation
- Wire transfer fraud
- Domain spoofing
- Spear phishing/whaling
Essentially, hackers use basic communications to siphon information and inject malware.
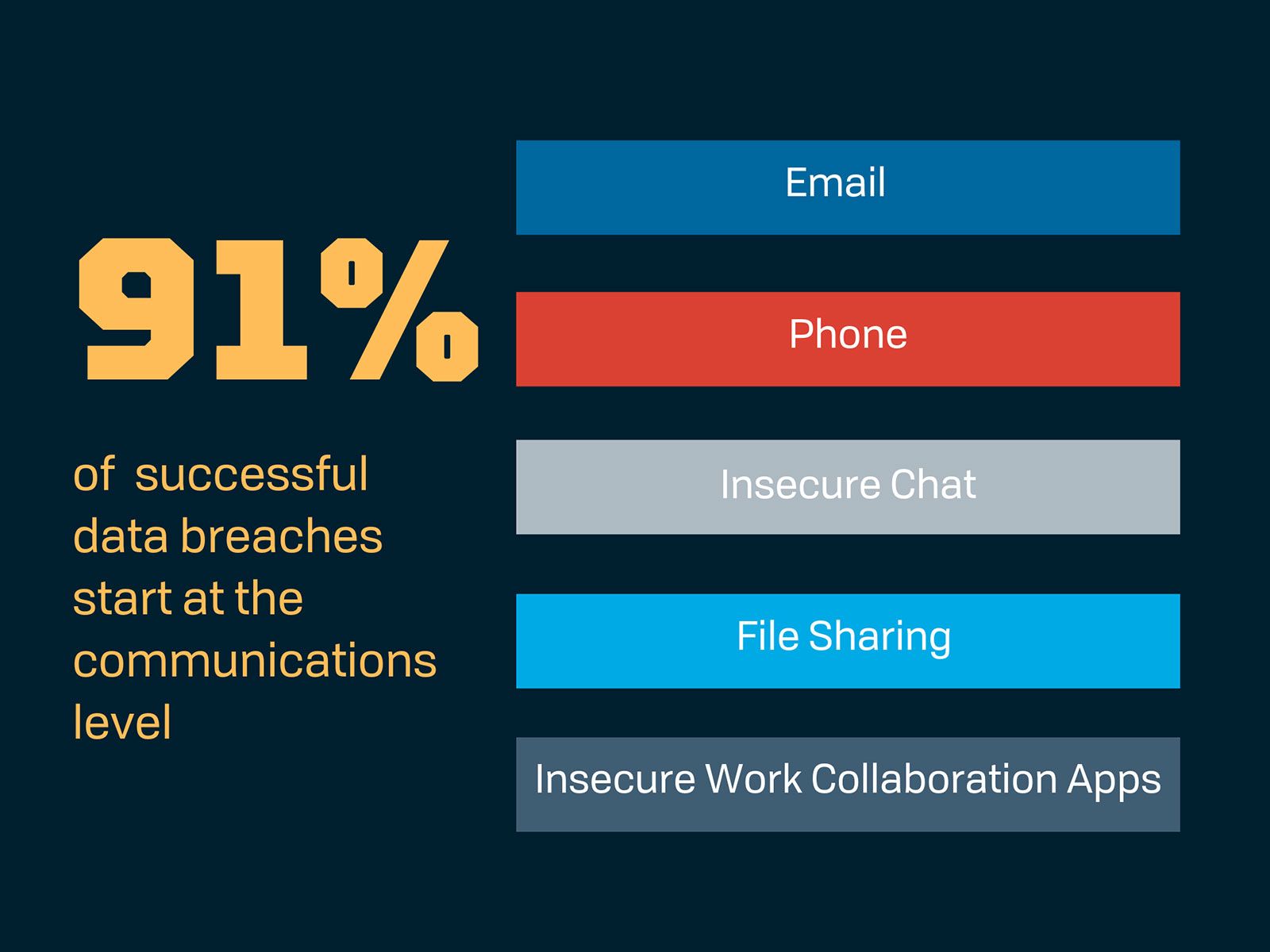
Email is the top conduit for malware with 92.4% of malware coming from email messages. Remember, the JP Morgan attack was initiated through phishing enabled malware on an employee computer.
Hackers are using phishing attacks to specifically target banks. A recent report shows that banking Trojans are the most prevalent types of malware delivered by email and constitute up to 82% of all malicious messages.
The right phishing email gives cyber criminals access to individual banking accounts, and in the worst cases, entire banking systems.
Man-in-the-Middle (MITM)
Financial institutions generally rely on TLS/SSL protocols to secure data as it’s passed digitally. The protocols encrypt data from the sender, unencrypt it at the service provider, and re-encrypt from the service provider to the recipient. The message is unencrypted at the recipient for the final time.
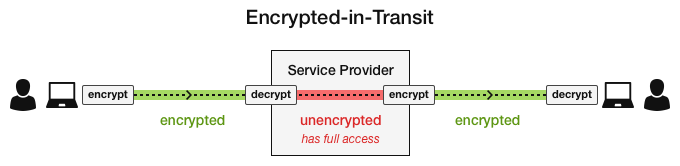
The obvious problem lies in the need to unencrypt data at the service provider. At that point, malicious insiders and other threat actors work as the man-in-the-middle and access messages containing sensitive information. That information gives direct access to financials, accounts, and institutions.
… Basically giving hackers the keys to the vault.
Solution
Smaller financial institutions may not have hundreds of millions of dollars to spend on cyber risk management.
But the good news is, they don’t need to.
JP Morgan was spending $250 million a year on cybersecurity when they suffered their historic breach. (They’ve since increased that to over $600 million).
The key isn’t spending the most money or having the largest IT staff. Financial institutions need careful consideration of cybersecurity and investments in the right places.
HighSide CEO Brendan Diaz explains it best.
“This is what we know… the tools banks are using to communicate, both internally among themselves and externally with customers, are insecure. The number of breaches, the fact that it’s getting worse year over year, suggests the anti-phishing ‘solutions’ enterprises like Microsoft and others are selling to banks aren’t working.”
In talking to Diaz, he emphasizes that communications attacks, specifically phishing, cause 9 out of 10 successful breaches.
“This is how malware gets in, bypassing the firewall. This is how wire fraud is initiated. It happens over and over again.”
Improving Basic Security
Basic cybersecurity involves determining risks. For banks, the risks lie heavily in email and MITM attacks.
Brendan Diaz illustrates a better way: HighSide.
“HighSide can help. It was designed to solve this problem, for banks. HighSide is not only immune to phishing and spoofing attacks, but helps prevent mass breaches, insider threats and even the prevalence of shadow IT/noncompliance.”
Secure Communications
HighSide is a secure communications platform that meets compliance standards required in financial industries. It utilizes a proprietary end-to-end encryption protocol that eliminates potential man-in-the-middle attacks and replaces email for secure communications. It has no concept of usernames and passwords for an attacker to phish and features a robust identity management system to prevent phishing and spoofing.
Bank employees know financial data and conversations are secure and hack-free through HighSide.
Bank leaders and executives know they’re protecting their institution’s reputation and bottom line while keeping their customer assets safe.
Contact a HighSide security specialist to learn how to improve your bank’s security, overcome likely cyber risks, and increase confidence in your customer base.
 Cecilia Clark
Cecilia Clark